
Three Pillars of Information Security: Confidentiality, Integrity, Availability
Do you know how every website and app asks for permission to access your data whenever you first create your account?
Or how some websites ask you to log in with your Google account?
Usually, we click on “I agree” without giving it a second thought.
But do you ever wonder what happens to all that data?
Is it secure or being used for some malicious purpose?
To use digital products and services, it sometimes becomes necessary to give access to our data. But what can we do to minimize the risks?
Experts urge us only to permit trusted websites to access our data.
Because they give priority to information security.
It is that one thing that protects our data from cyberattacks.
Fundamentally, there are three pillars of Information Security.
And today, we are going to discuss them in detail.
What are the Three Pillars of Information Security?
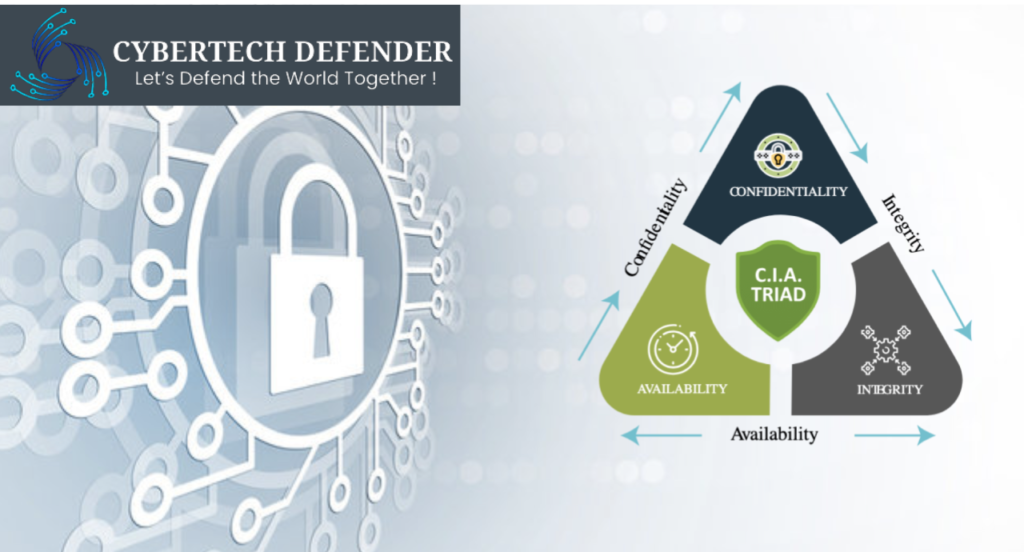
To understand the concept of the three pillars of information security, we’ll compare it with a three-legged tool. The legs are Confidentiality (keeping data private), Integrity (keeping data accurate), and Availability (making sure you can access your data when you need to).
Just like a stool, we need these three pillars to be strong and resilient. Even if one leg gets weak, then the entire thing falls.
They are also interconnected with each other. If there is an impact on one of the pillars, it affects the other two too.
Let’s take another example to understand this.
If someone steals your personal data (this impacts confidentiality), they might use it to execute a crime or for financial gain (this impacts integrity). Or, maybe they mess with the system so much that you can’t access your information (this impacts availability).
So, all three parts of information security are important and need to be protected!
Let’s understand the three of them.
Confidentiality
Suppose you have a journal where you note your feelings, wants, purpose, and everything close to you. Now, you wouldn’t leave it open on a park bench for anyone to read it, would you?
You’ll allow only a handful of people to have access to it.
The same goes for your digital data.
Confidentiality is about making sure that only the right people can see your sensitive information.
What happens when confidentiality is breached?
If there is a breach of confidentiality, it can have serious consequences:
- Identity theft: Hackers can use your personal information to open new accounts, take out loans, or commit other crimes in your name.
- Financial loss: They can use your bank account and debit/credit cards to steal your money.
- Reputational damage: Leaked private information or embarrassing photos can ruin your reputation and relationships.
- Legal consequences: Companies can face hefty fines and lawsuits for failing to protect customer data.
How do we keep things confidential?
There are several ways to ensure confidentiality:
- Encryption: This scrambles your data into a secret code that only those with the right key (or password) can unlock.
- Access controls: These make sure only authorized users can see or change certain information.
- Physical security: This involves protecting the actual devices and storage media where your data is. That includes locked doors, security cameras, and secure data centers.
READ MORE: Top Cybersecurity Trends
Integrity
Integrity makes sure your data stays accurate and unchanged, except by those who are authorized to do so. It prevents any unwanted tampering or meddling with your information.
Real-World Impacts of Breach in Data Integrity
Data integrity breaches can have serious consequences. Here are a few examples:
- Data Tampering: If someone maliciously alters financial records, it could lead to significant losses or even fraud.
- Ransomware: This malware encrypts your files and makes them inaccessible unless you pay a ransom. It’s a direct attack on data integrity.
- Software Supply Chain Attacks: If hackers insert malicious code into software updates, it can compromise the integrity of entire systems. This could lead to widespread damage.
How Do We Keep Data ‘Honest’
There are a few techniques used to maintain data integrity:
- Checksums: A checksum is a value that’s calculated from data to verify its authenticity and integrity. If even a tiny bit of the value changes, that would mean someone has tampered with the file.
- Version Control: With this, you can track every change made, and if something goes wrong, you can easily revert to an earlier, untampered version.
- Access Controls: Only authorized people should be able to change data. Strict access controls ensure that only the right people have the keys to make modifications.
YOU MAY ALSO LIKE: Understanding and Combating AI Hacking
Availability
Suppose you need to access an important file for work, but the system is down. Or you try to make an online purchase, but the website is unavailable.
It’s frustrating, right?
That’s where availability comes in.
In information security, availability means making sure that authorized users can access the data and resources they need when they need them.
What Happens When Availability Goes Wrong
When availability fails, it can have serious consequences. Here are a couple of examples:
- Denial-of-Service (DoS) Attacks: These attacks flood a system with so much traffic that it becomes overwhelmed and can’t respond to legitimate requests.
- System Outages: These can happen for many reasons, like hardware failures, software bugs, or even natural disasters. When a system goes down, it can disrupt business operations, cause financial losses, and even put people’s lives at risk.
How to Keep Things Available
So, how do we make sure things stay available? There are a few key strategies:
- Redundancy: It’s like having a backup plan. If one system fails, another one is ready to take over.
- Backups: Regularly backing up your data is highly effective. If something happens to your original data, you’ll have a copy you can restore.
- Disaster Recovery Plans: This is a detailed plan for how to get things back to normal after a major incident.
ALSO READ: Cybersecurity Training in India
Secure Your Digital Future and Career with an Information Security Course
You’ve just explored the three pillars of information security—confidentiality, integrity, and availability. If any one of these pillars weakens, the whole structure is at risk.
Today, cybersecurity isn’t just a tech issue, it’s everyone’s responsibility. Understanding these fundamentals empowers you to make informed decisions and take proactive steps to protect your sensitive information.
Ready to Take the Next Step?
If you’re serious about safeguarding your digital assets and building a career in cybersecurity, consider exploring the comprehensive course on Information Security offered by CyberTech Defender.
Our expert-led training programs will give you the in-depth knowledge and practical skills you need to become a cybersecurity champion.
Don’t wait for a breach to happen. Empower yourself with knowledge and take control of your security today!



